Token Based Authentication In Webapi
Planning ahead is the secret to staying organized and making the most of your time. A printable calendar is a simple but effective tool to help you map out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Token Based Authentication In Webapi
The Printable Calendar 2025 offers a clean overview of the year, making it easy to mark appointments, vacations, and special events. You can hang it up on your wall or keep it at your desk for quick reference anytime.

Token Based Authentication In Webapi
Choose from a range of stylish designs, from minimalist layouts to colorful, fun themes. These calendars are made to be user-friendly and functional, so you can stay on task without clutter.
Get a head start on your year by grabbing your favorite Printable Calendar 2025. Print it, customize it, and take control of your schedule with clarity and ease.

31 WEB API Token Based Authentication In Telugu YouTube
token token 8 Java 42 2 72 1 Token session 会话机制 token 会话机制 三、Cookie、Session和Token Cookie(浏览器缓存) 1.什么是Cookie Cookie 实际上是一小段的 文本信息。 客户端请求服务器,如果服务器需要记录该用户状态,就使用response向客户端浏览器颁发一个Cookie。 客户端浏览器会把Cookie保存起来。

JWT Token With RBAC Role Based Access Control In ASP NET Core WebAPI
Token Based Authentication In Webapitoken也可以由patch embedding得到(你可以去看看 2022年 CVPR 的 MixFormer),但是token貌似比patch要小一点,有的地方说token可以理解为一个像素,并且包含该像素点的位置和类别信息,总的来说就是和patch类似,但是比patch的尺寸小,包含的信息多一点。 Token Token JWT JSON Web Token Token JSON Token
Gallery for Token Based Authentication In Webapi

Token Based Authentication JWT In Asp Core 2 0 WebAPI YouTube
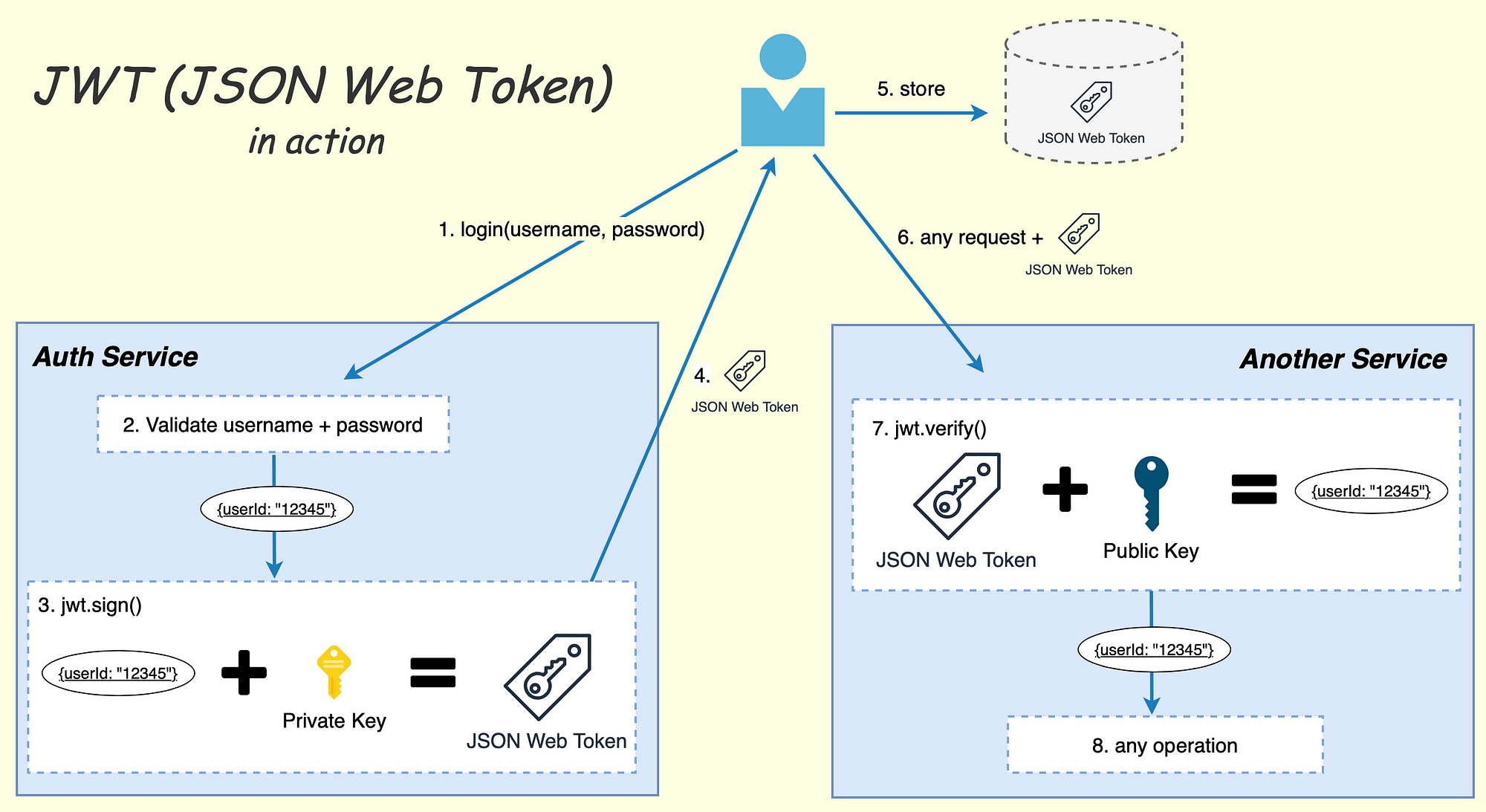
Clean Architecture JWT Token Authentication In REST API 45 OFF

Api party Nuxt Modules

GitHub EnesSERENLI AnadoluParamApi Management This Project Is A

Security Token Based Authentication Warewolf Knowledge Base

SWAGGER UI Enable Token Based Authentication In Spring Boot

GitHub CoreProgramm token based authentication in Web API Token

GitHub CoreProgramm token based authentication in Web API Token

Asp Net Core 3 0 Web API Token Based Authentication Example Using JWT

What Is Token Based Authentication Types Pros And Cons