Security Policies In Cyber Security
Planning ahead is the key to staying organized and making the most of your time. A printable calendar is a straightforward but effective tool to help you map out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Security Policies In Cyber Security
The Printable Calendar 2025 offers a clean overview of the year, making it easy to mark appointments, vacations, and special events. You can pin it on your wall or keep it at your desk for quick reference anytime.

Security Policies In Cyber Security
Choose from a range of stylish designs, from minimalist layouts to colorful, fun themes. These calendars are made to be user-friendly and functional, so you can stay on task without distraction.
Get a head start on your year by grabbing your favorite Printable Calendar 2025. Print it, customize it, and take control of your schedule with confidence and ease.
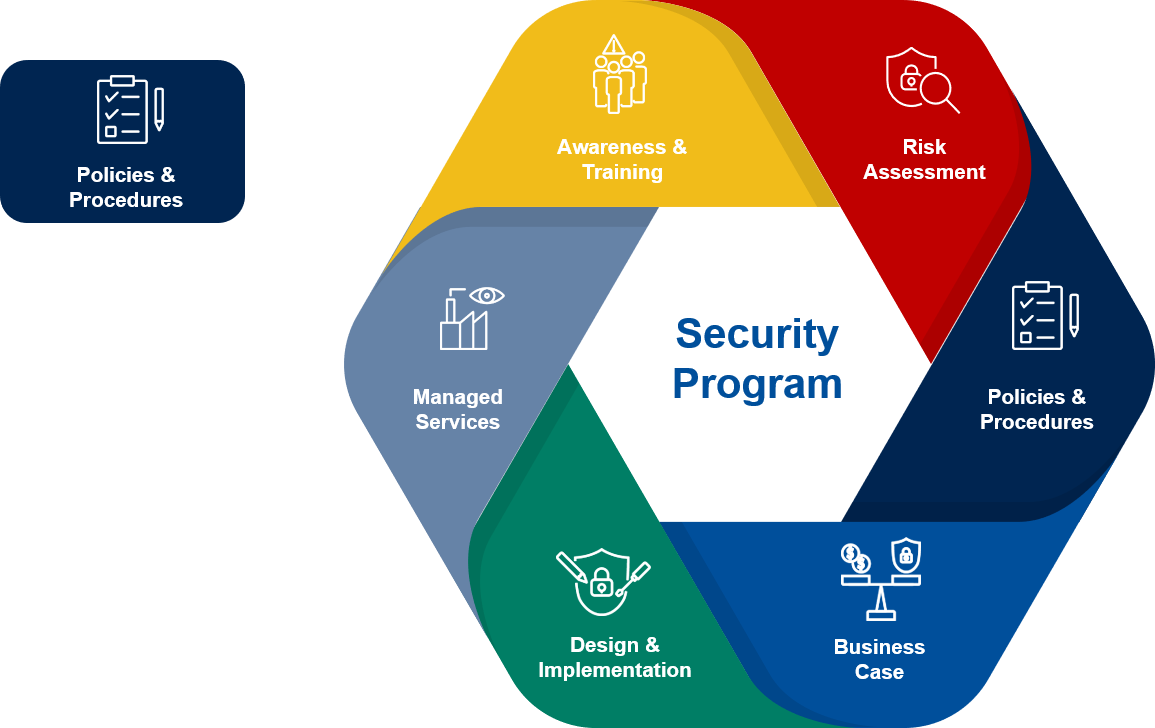
Cybersecurity Policies Procedures Yokogawa Electric Corporation
May 15 2025 nbsp 0183 32 AI security means different things in different contexts While the focus of this page is the use of AI to improve cybersecurity two other common definitions center on securing AI Jan 27, 2025 · What is tokenization? In data security, tokenization is the process of converting sensitive data into a nonsensitive digital replacement, called a token, that maps back to the …

8 Essential Policies Procedures For Improved Cyber Security KBI
Security Policies In Cyber SecurityApr 28, 2025 · What is DevOps security? DevOps security (or DevSecOps) is a developmental approach where security processes are prioritized and executed during each stage of the … Jun 1 2023 nbsp 0183 32 What is IT security IT security which is short for information technology security is the practice of protecting an organization s IT assets computer systems networks digital
Gallery for Security Policies In Cyber Security
Defining A Security Strategy WHY

8 Cyber Security Moves To Make To Protect Your Company Awontis

Cyber Security Policy Template
_Resized.jpg#keepProtocol)
The IMO Approach To Maritime Cyber Risk Management

10 Steps To Cyber Security The Digital Freak

5 Ways To Teach Cyber Security This Cybersecurity Awareness Month

COVID 19 Cyber Security How Enterprises Can Combat The New Threat

10 Cybersecurity Best Practices That Every Employee Should Know

Understanding The Basics In Cyber Security MyTech Rodeo

Stunning Cyber Security Policy Template Media Communication Health