Message Authentication In Information Security
Planning ahead is the key to staying organized and making the most of your time. A printable calendar is a straightforward but powerful tool to help you map out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Message Authentication In Information Security
The Printable Calendar 2025 offers a clean overview of the year, making it easy to mark meetings, vacations, and special events. You can pin it on your wall or keep it at your desk for quick reference anytime.

Message Authentication In Information Security
Choose from a variety of modern designs, from minimalist layouts to colorful, fun themes. These calendars are made to be easy to use and functional, so you can focus on planning without distraction.
Get a head start on your year by downloading your favorite Printable Calendar 2025. Print it, customize it, and take control of your schedule with clarity and ease.

Message Authentication Code MAC And HMAC Cryptography Cyber
RCS chats Offer read receipts which show when someone has read or received your message Read receipts also show your contact when you read their message When you use RCS On your device, open Google Messages . Tap Get Started Next. To keep Google Messages connected, tap Yes. If you can't turn on RCS chats, learn how to troubleshoot.

Authenticate
Message Authentication In Information SecurityChange advanced settings Change how Google Messages sends pictures, videos & audio files Send a message or a file separately to each person in a conversation: Tap Group messaging … Avec Google Messages pour le Web vous pouvez discuter avec vos amis depuis votre ordinateur ou votre tablette Android Vous avez acc 232 s 224 tous les contenus de votre application mobile
Gallery for Message Authentication In Information Security
Authentication Definition

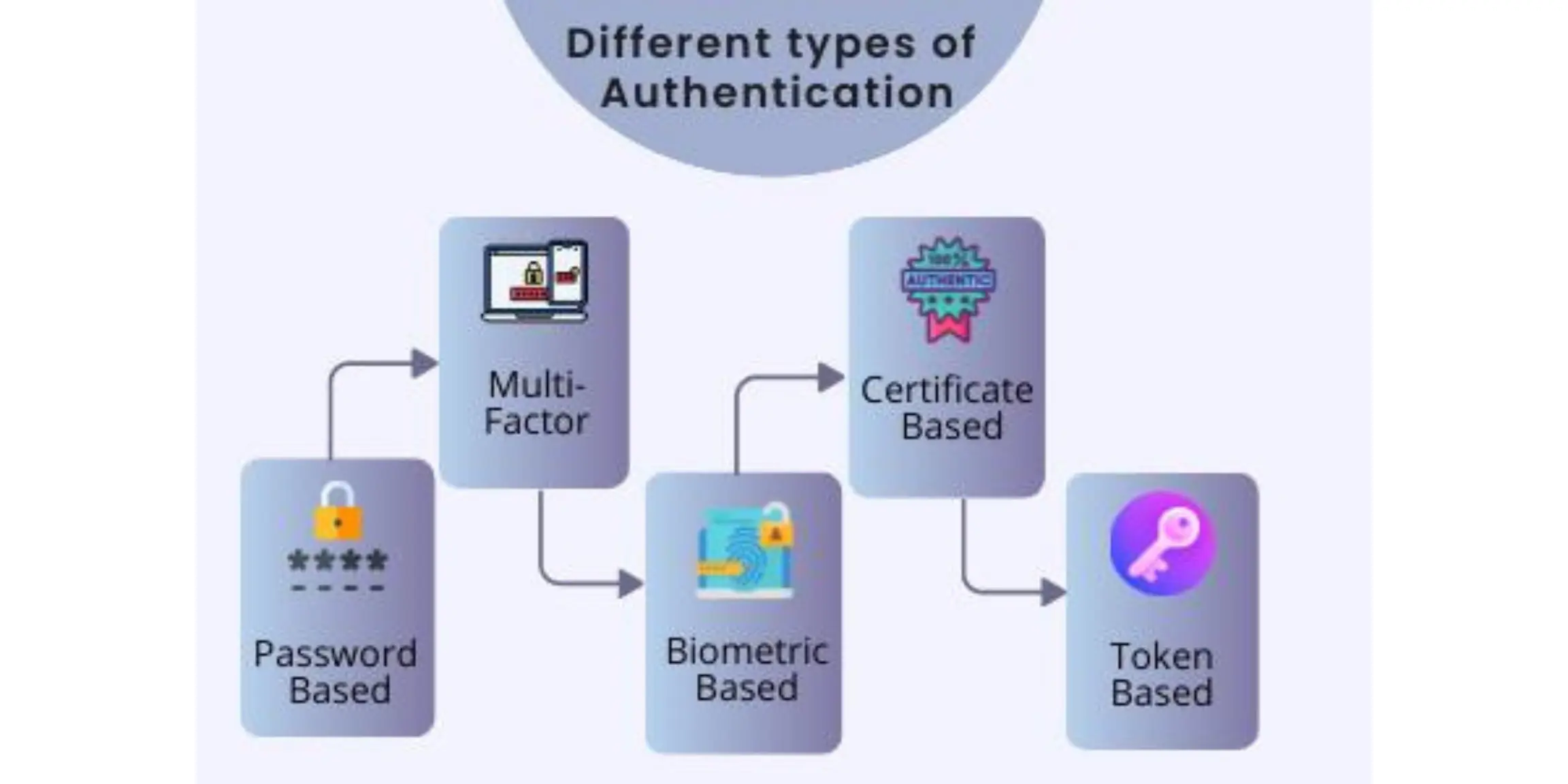
Multifactor Authentication
Authentification
Authentication

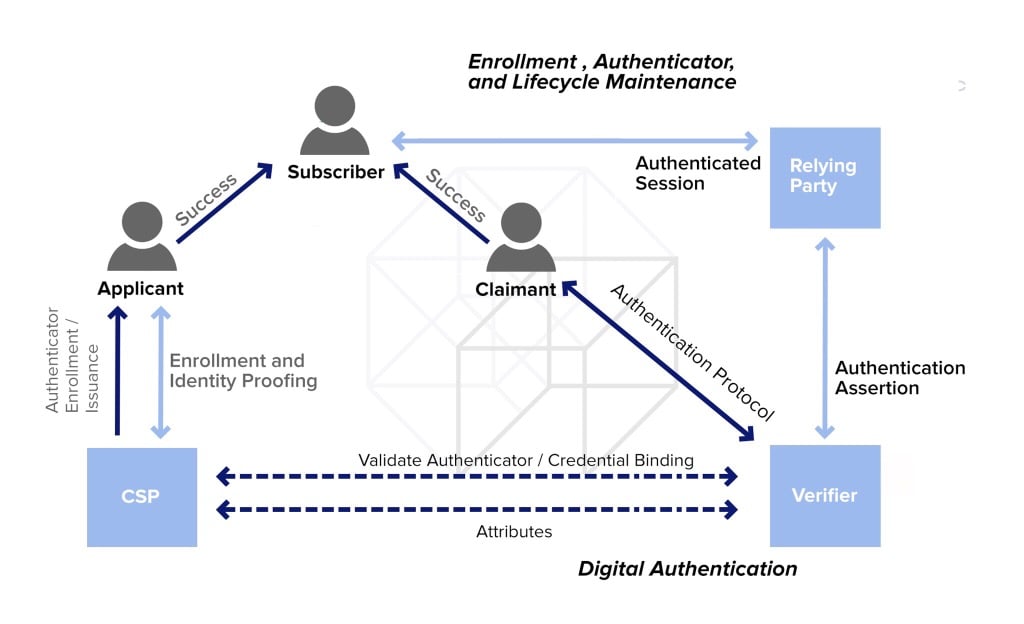
What Is Authentication Types Roles How It Works

Block Cipher Message Authentication Code Download Scientific Diagram
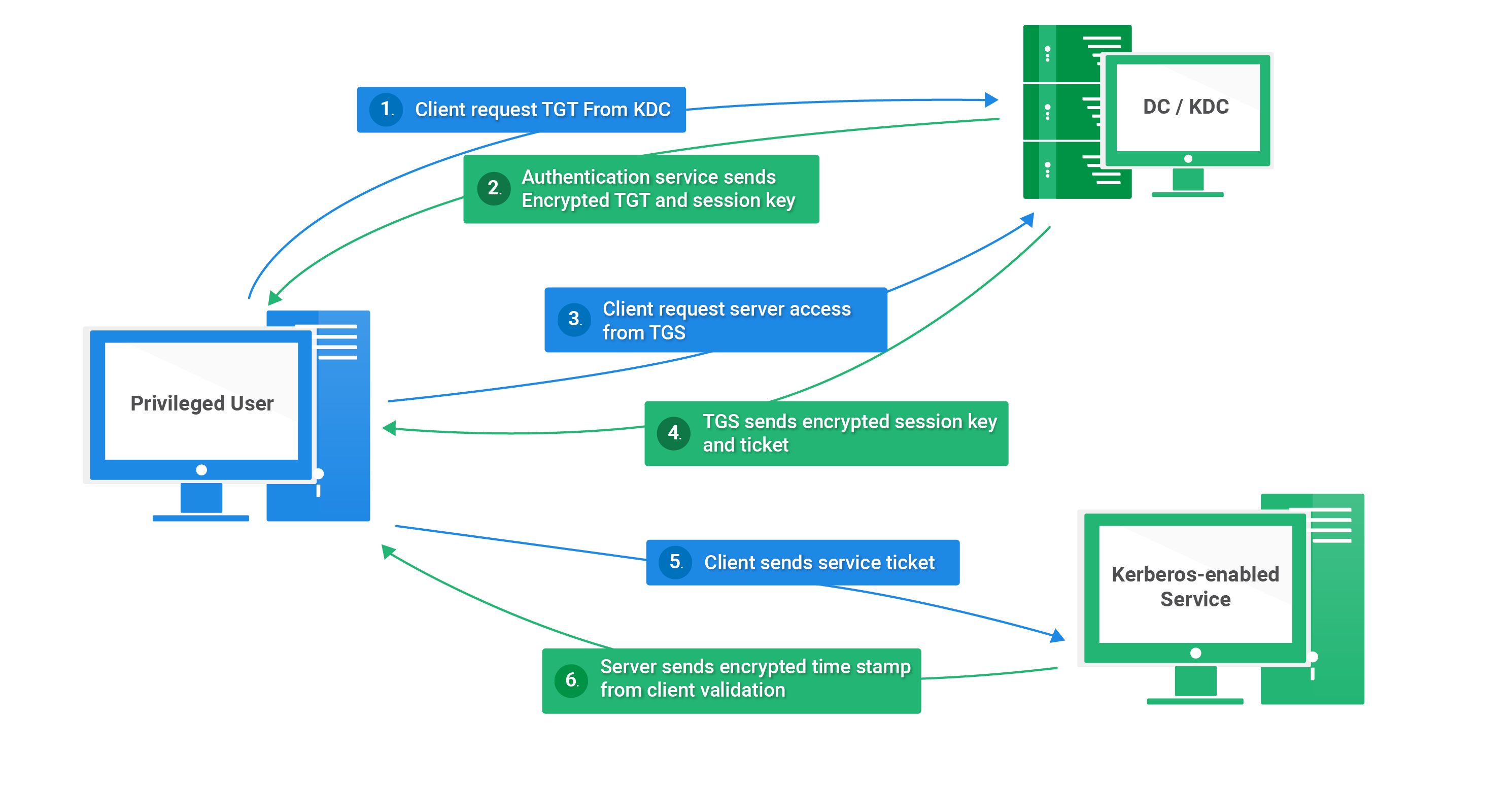
Kerberos Fundamentals What It Is And How It Works QOMPLX
Authentication Security

Chapter 15 Security Ppt Download
+Note+symmetric+cryptography+based+on+transformations%2C+asymmetric+based+on+mathematical+functions..jpg)
Chapter 15 Security Ppt Download