Known Exploited Vulnerabilities Definition
Planning ahead is the secret to staying organized and making the most of your time. A printable calendar is a simple but powerful tool to help you map out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Known Exploited Vulnerabilities Definition
The Printable Calendar 2025 offers a clean overview of the year, making it easy to mark appointments, vacations, and special events. You can hang it up on your wall or keep it at your desk for quick reference anytime.

Known Exploited Vulnerabilities Definition
Choose from a range of modern designs, from minimalist layouts to colorful, fun themes. These calendars are made to be user-friendly and functional, so you can stay on task without distraction.
Get a head start on your year by downloading your favorite Printable Calendar 2025. Print it, personalize it, and take control of your schedule with clarity and ease.
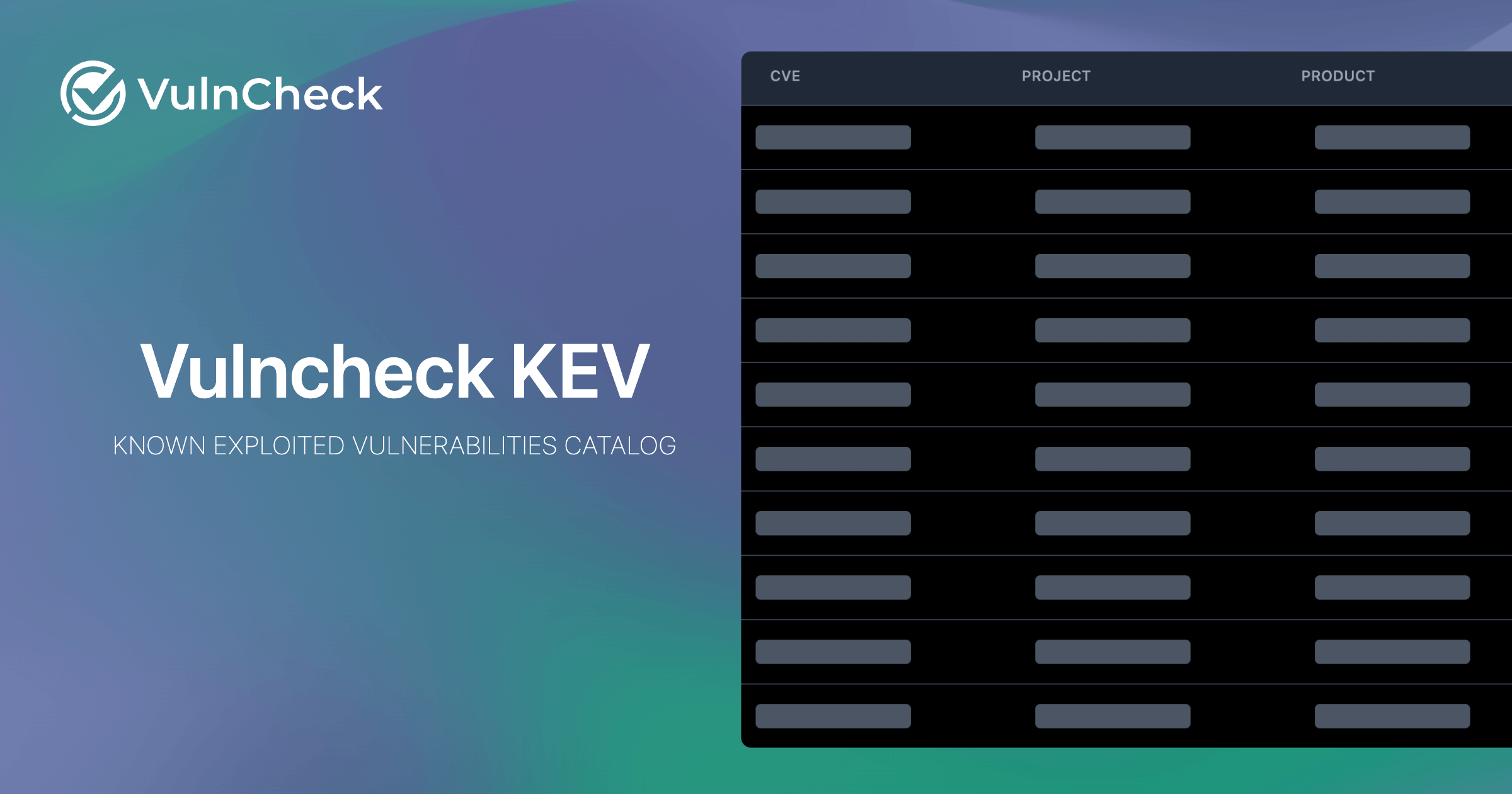
Known Exploited Vulnerabilities Catalog VulnCheck
Dec 11 2023 nbsp 0183 32 In its conclusions and recommendations the Committee says the Home Office must not conflate immigration with human trafficking and modern slavery at the expense of Modern slavery and human trafficking are crimes. Contact the police if you or someone you know is in immediate danger or a victim of human trafficking or modern slavery.

NVD Home
Known Exploited Vulnerabilities DefinitionIt looks likely that the number of victims of modern slavery globally will continue to rise over the coming years. It is vital that we educate potential victims about the risks, how to avoid... We offer digital advice to help people understand whether they or someone they know may have been a victim of human trafficking signpost them to specialist support organisations and
Gallery for Known Exploited Vulnerabilities Definition

CISA Known Exploited Vulnerabilities What To Know VMiss
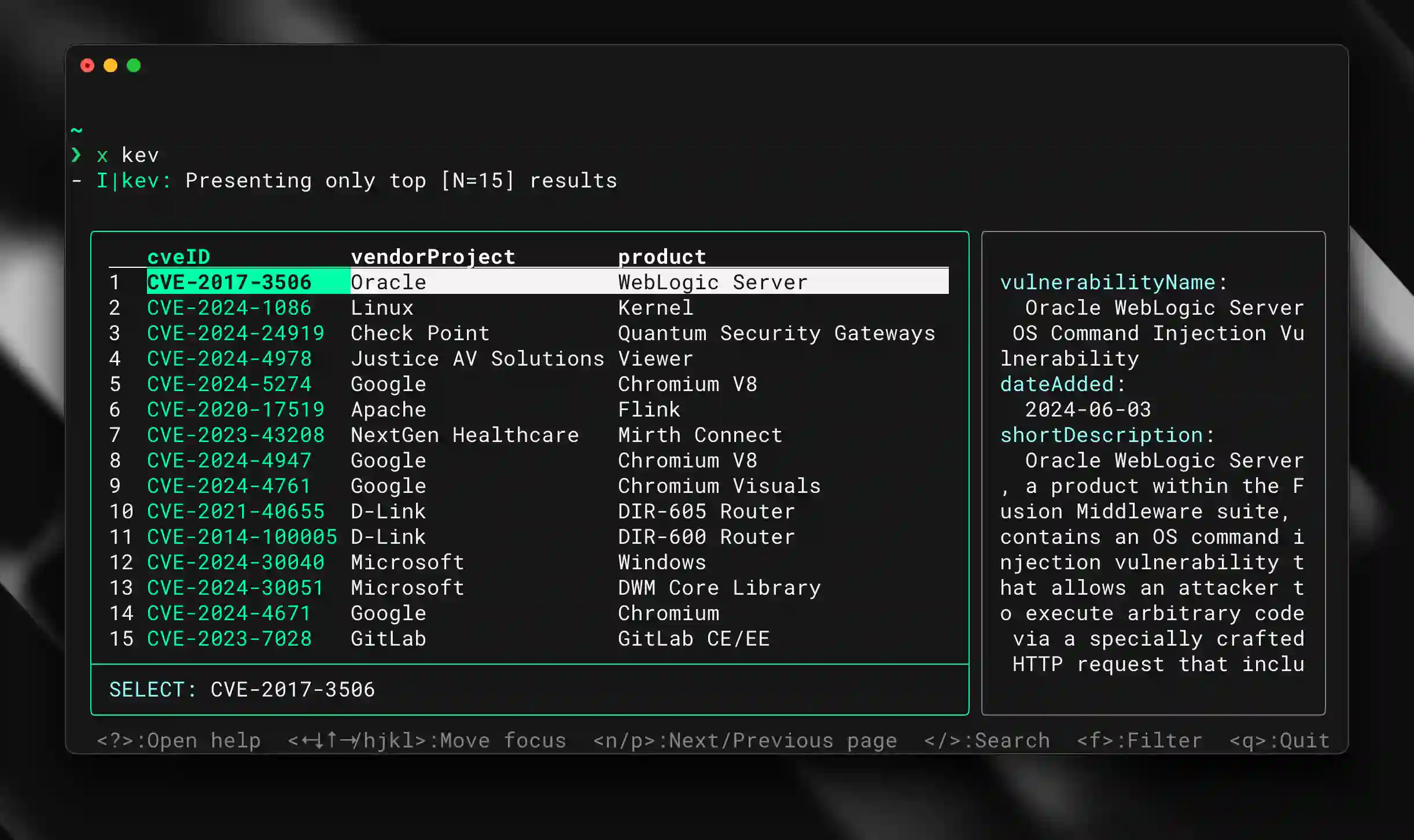
X Kev X cmd Mod KEV Catalog Known Exploited Vulnerabilities
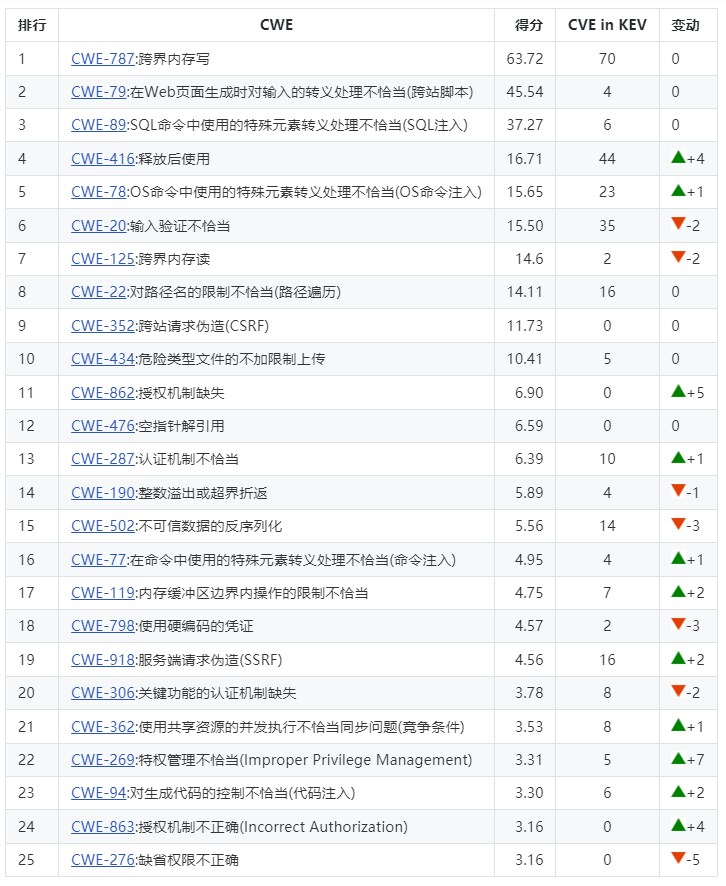
2023 25 CWE TOP 25

Ransomware In 2024 What CISOs Must Know SC Media
What Are Known Exploited Vulnerabilities XM Cyber

How Does The Idea Of Vulnerabilty Debelop Over Tiem Clearance

Zero Day Vulnerabilities CyberHoot

Network Layer Model

Prioritizing CISA Known Exploited Vulnerabilities Blog VulnCheck

Cybernews 2023 KER