Identity Access Governance
Planning ahead is the key to staying organized and making the most of your time. A printable calendar is a straightforward but effective tool to help you map out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Identity Access Governance
The Printable Calendar 2025 offers a clean overview of the year, making it easy to mark appointments, vacations, and special events. You can hang it up on your wall or keep it at your desk for quick reference anytime.

Identity Access Governance
Choose from a variety of stylish designs, from minimalist layouts to colorful, fun themes. These calendars are made to be easy to use and functional, so you can focus on planning without clutter.
Get a head start on your year by grabbing your favorite Printable Calendar 2025. Print it, personalize it, and take control of your schedule with confidence and ease.

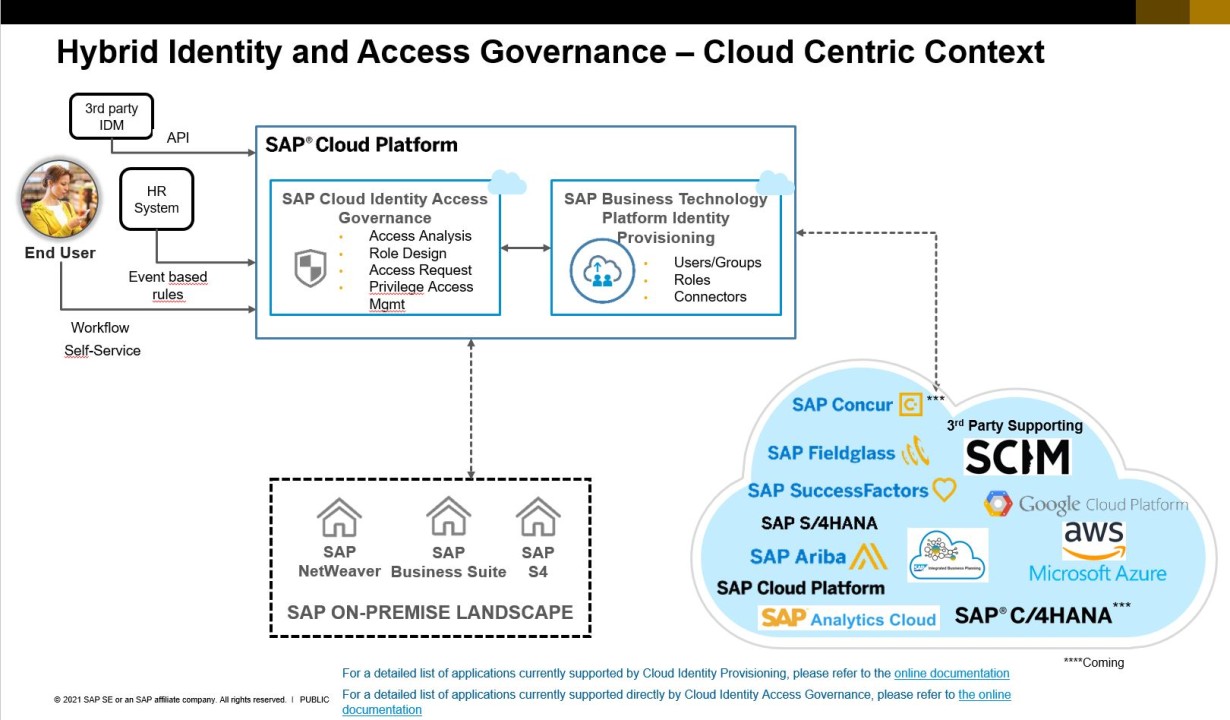
SAP Cloud Identity Access Governance Managing Access Risks
VIS Visual Identity System MI Jan 30, 2008 · Buenas tardes: Dudo sobre la traducción de "Tarjeta de Identidad de extrangero (NIE)"... foreigner identity cord (NIE)??, no se refiere al documento de identificación de un país …

SAP Cloud Identity Access Governance IAG Training Mentors Pool
Identity Access Governanceidentification和identity有以下区别: 1、表示的意思不同。 identity表示身份。 identification表示认同、确认;鉴定、识别;身份证明。 2、用法不同 identification用在表示认同、确认;鉴定、 … Identity ID identify
Gallery for Identity Access Governance

SAP Cloud Identity Access Governance IAG Training Mentors Pool

Identity Access Governance Mobius Consulting MU

SAP Cloud Identity And Access Governance IAG Begin By SAP PRESS

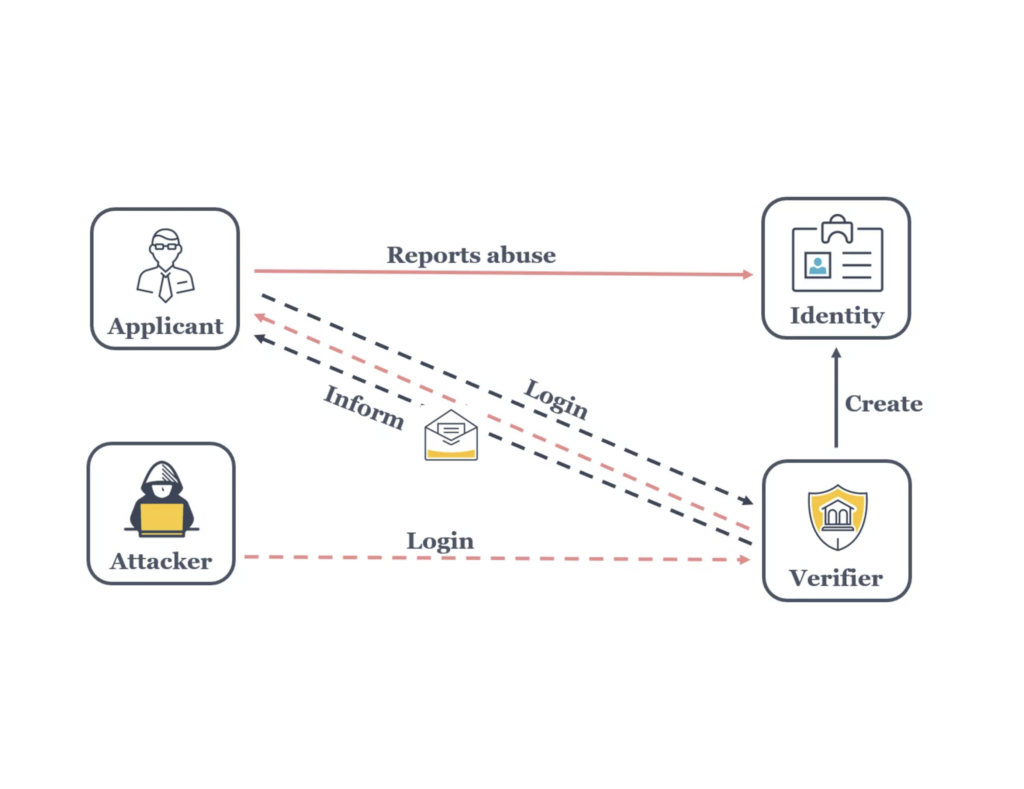
The Essential Role Of Identity Access Governance SafePaaS
SAP Cloud Identity Access Governance Initial Setup
Understanding SAP Cloud Identity Access Governance Solutions
How To Implement SAP Cloud Identity Access Governance SAPinsider

Identity Access Governance Framework Ppt Powerpoint Presentation
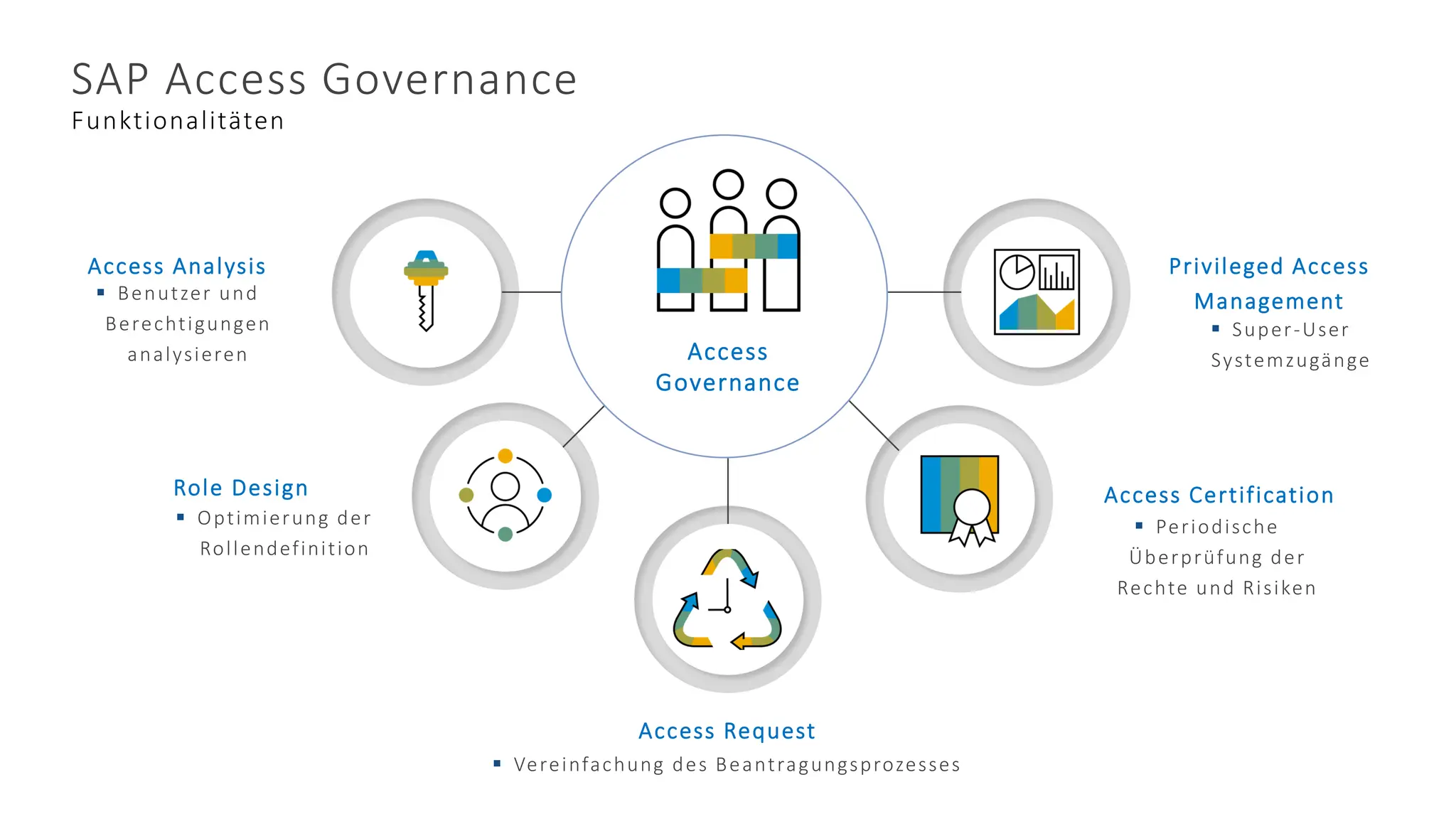
SAP Cloud Identity Access Governance Vs SAP Access Control Updates

Navigating The New Frontier Strengthening Cybersecurity Through Next