Hackers Exploiting Microsoft 365 Oauth Meaning
Planning ahead is the key to staying organized and making the most of your time. A printable calendar is a simple but powerful tool to help you map out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Hackers Exploiting Microsoft 365 Oauth Meaning
The Printable Calendar 2025 offers a clean overview of the year, making it easy to mark appointments, vacations, and special events. You can pin it on your wall or keep it at your desk for quick reference anytime.
Hackers Exploiting Microsoft 365 Oauth Meaning
Choose from a range of modern designs, from minimalist layouts to colorful, fun themes. These calendars are made to be easy to use and functional, so you can stay on task without clutter.
Get a head start on your year by downloading your favorite Printable Calendar 2025. Print it, personalize it, and take control of your schedule with clarity and ease.

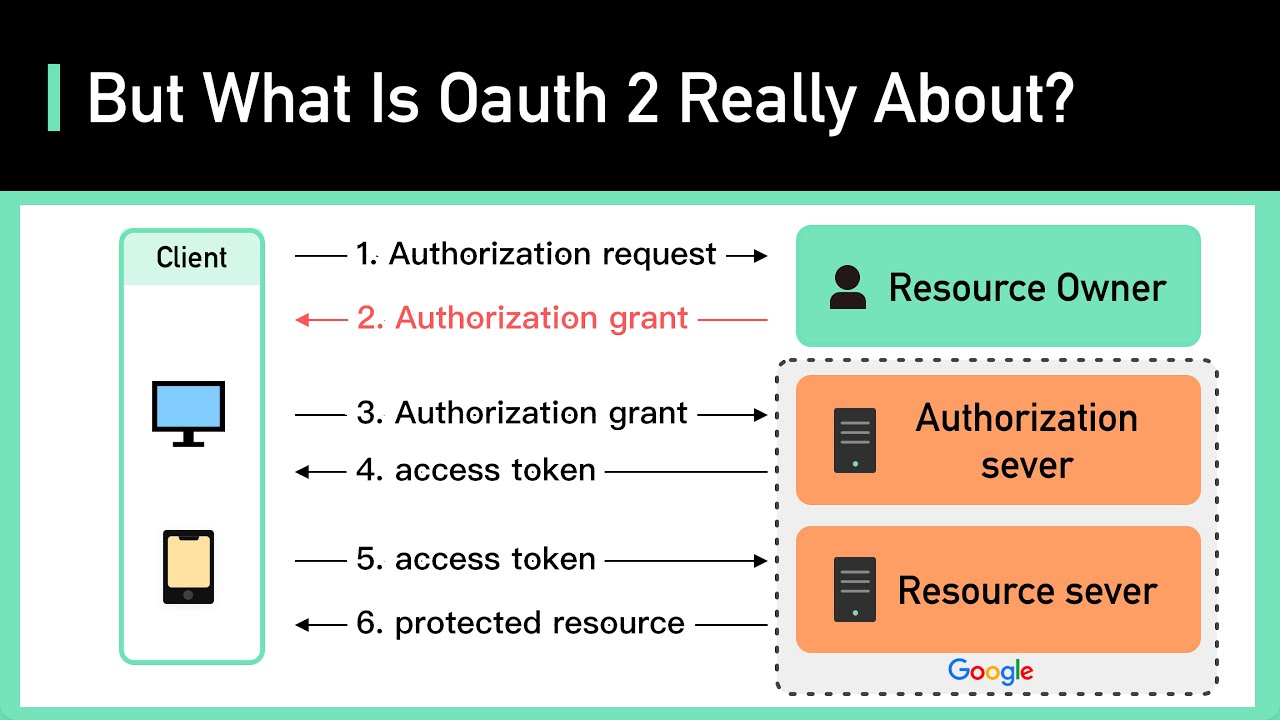
Office 365 IMAP OAuth With C YouTube
Aug 8 2008 nbsp 0183 32 Hackers do laundry Hackers like movies Hackers are people and could be your neighbors your brother your friends Presenting a portrait of the hacking community created Sep 15, 1995 · 达德(约翰·李·米勒 Jonny Lee Miller 饰)是一名出色的天才黑客,曾经,股市因为11岁的他的小小恶作剧而差点崩盘,达德因此被剥夺了使用网络的权利,如今,已经成年的达 …

Microsoft 365 OAuth Authentication
Hackers Exploiting Microsoft 365 Oauth MeaningFeb 10, 2016 · Memory. Whether it’s sharp, fuzzy, poignant, or thrilling, it’s the glue that binds our mental lives... Jun 12 2010 nbsp 0183 32 Hackers Wanted Hackers Wanted
Gallery for Hackers Exploiting Microsoft 365 Oauth Meaning
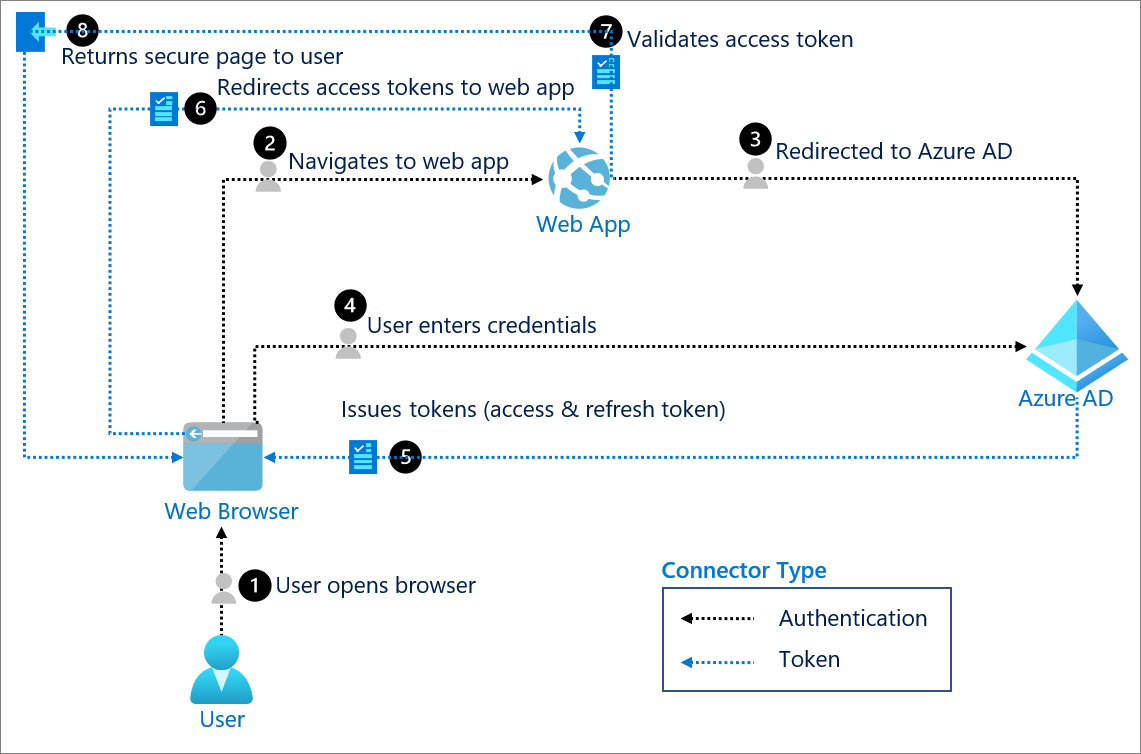
Microsoft Aborda La Falla NOAuth De Azure AD Que Permite La Adquisici n
Alert Hackers Exploiting CrowdStrike Issue In Cyber Attacks
CrowdStrike AI Tool For Cybersecurity

CSO Online Windows Security Tips

Hackers Exploiting MS SQL Severs To Deploy Mallox Ransomware
Exploiting Microsoft Rewards Be Like Fandom
Hackers Exploiting Microsoft 365 OAuth Workflows To Target Organizations

Hackers Exploiting Microsoft 365 OAuth Workflows To Target Organizations
Volt Typhoon Attacks On US Critical Infrastructure Paul Bergman
Hackers Bypass MFA In Microsoft 365