Function Approximation Methods
Planning ahead is the key to staying organized and making the most of your time. A printable calendar is a straightforward but powerful tool to help you map out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Function Approximation Methods
The Printable Calendar 2025 offers a clear overview of the year, making it easy to mark appointments, vacations, and special events. You can pin it on your wall or keep it at your desk for quick reference anytime.

Function Approximation Methods
Choose from a variety of modern designs, from minimalist layouts to colorful, fun themes. These calendars are made to be easy to use and functional, so you can stay on task without distraction.
Get a head start on your year by downloading your favorite Printable Calendar 2025. Print it, customize it, and take control of your schedule with clarity and ease.

PDF Control Volume Function Approximation Methods And Their
Jul 16 2025 nbsp 0183 32 Starting in R81 20 these are the responsibilities of the different daemons vpnd iked and cccd The VPN daemon quot vpnd quot Tunnel Test 48234 48297 UDP Check Point RDP 30259 30322 UDP L2TP 31701 31764 UDP CLI Syntax to control the IKE daemon quot iked quot Jul 16, 2025 · Tunnel Testing for Permanent Tunnels. Check Point uses a proprietary protocol to test if VPN tunnels are active, and supports any site-to-site VPN configuration. Tunnel testing requires two Security Gateways, and uses UDP port 18234. Check Point tunnel testing protocol does not support 3rd party Security Gateways. Terminating Permanent Tunnels
Approximation Methods For Bilevel Programming Saeed Ghadimi Mengdi
Function Approximation MethodsNov 4, 2024 · VPN Tunnel View Updates. If a Tunnel is deleted from SmartConsole Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., the Tunnel Results View shows the deleted Tunnel for an hour after it was deleted.. If a community is edited, the … May 10 2025 nbsp 0183 32 Starting in R81 20 these are the responsibilities of the different daemons vpnd iked and cccd The VPN daemon quot vpnd quot Tunnel Test 48234 48297 UDP Check Point RDP 30259 30322 UDP L2TP 31701 31764 UDP CLI Syntax to control the IKE daemon quot iked quot
Gallery for Function Approximation Methods

MATLAB Logical Operators 1 2 YouTube

MATLAB Logical Expression Tutorial YouTube
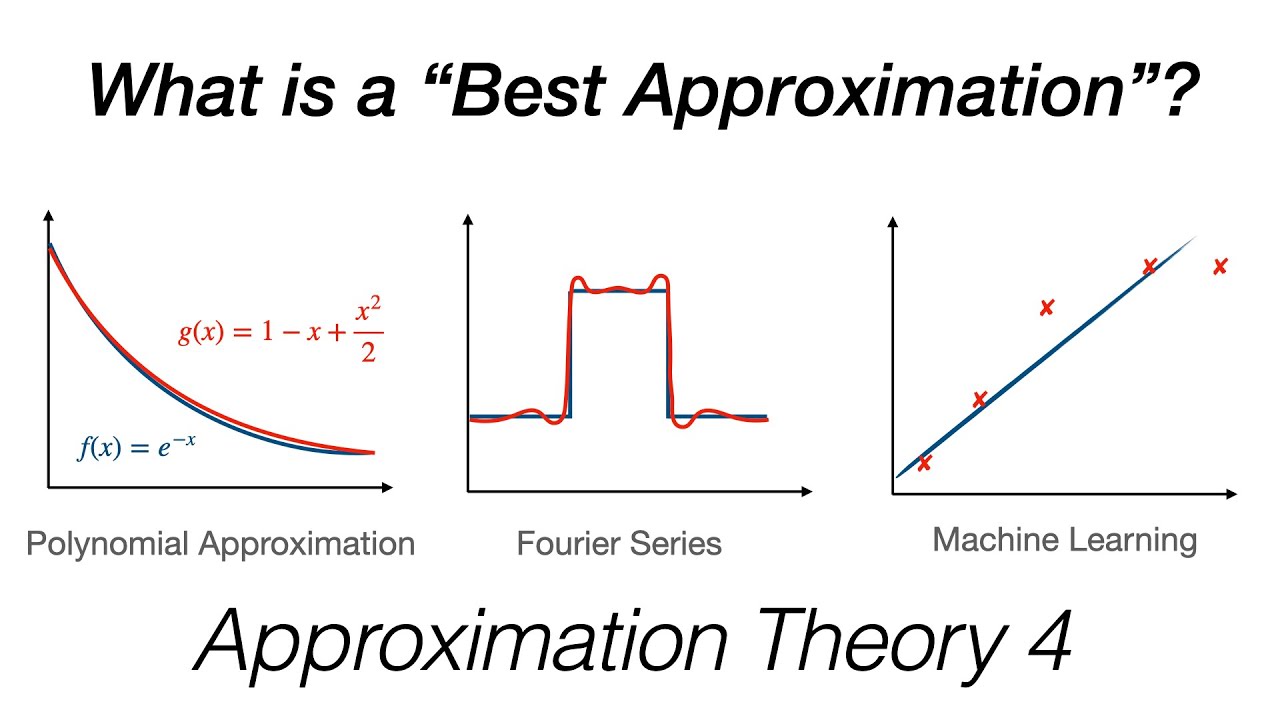
Approximating Functions In A Metric Space YouTube

Function Approximation Using Data Fitting Neural Network

Approximate Integration Example 3 Midpoint Rule YouTube

Approximating Functions Using Taylor Series Methods YouTube

Linear Approximation Differential AP Calculus For Exponential Function

Approximating A Nonlinear Function By A Linear Function YouTube

From Signal Processing To Machine Learning Ppt Download
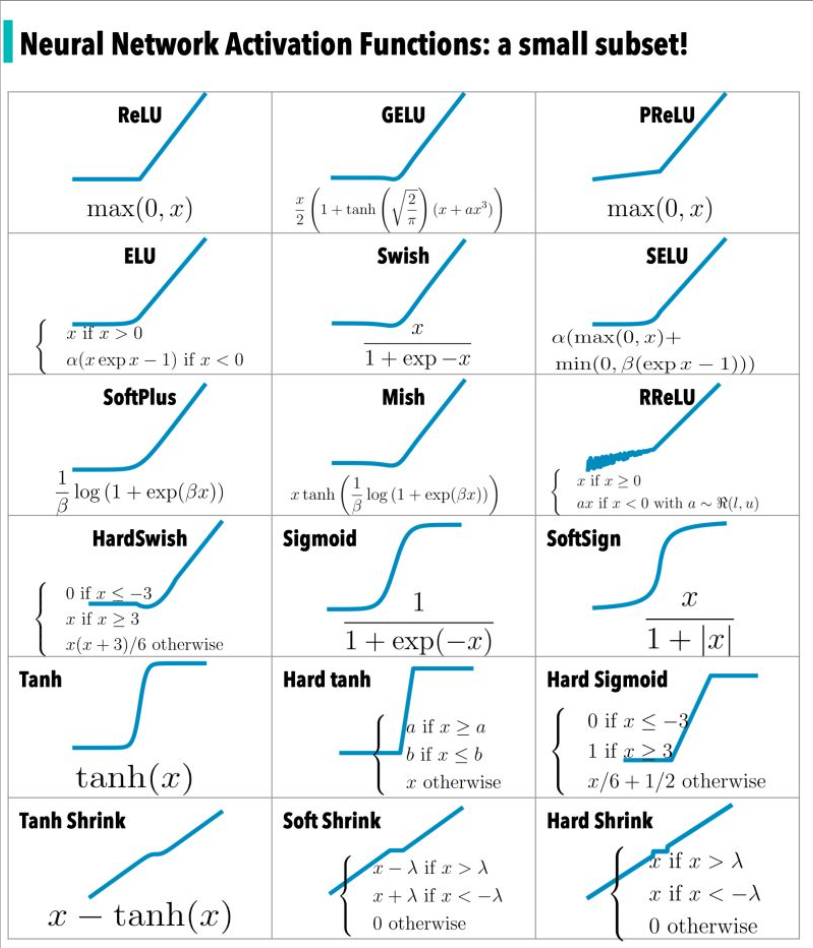
Vinija s Notes Primers Activation Functions
