Exploiting Format String Vulnerabilities Examples
Planning ahead is the secret to staying organized and making the most of your time. A printable calendar is a simple but powerful tool to help you lay out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Exploiting Format String Vulnerabilities Examples
The Printable Calendar 2025 offers a clean overview of the year, making it easy to mark appointments, vacations, and special events. You can pin it on your wall or keep it at your desk for quick reference anytime.

Exploiting Format String Vulnerabilities Examples
Choose from a range of stylish designs, from minimalist layouts to colorful, fun themes. These calendars are made to be user-friendly and functional, so you can stay on task without clutter.
Get a head start on your year by downloading your favorite Printable Calendar 2025. Print it, personalize it, and take control of your schedule with clarity and ease.

Introduction To Format String Vulnerabilities YouTube
You can translate text handwriting photos and speech in over 200 languages with the Google Translate app You can also use Translate on the web You can translate text, handwriting, photos, and speech in over 200 languages with the Google Translate app. You can also use Translate on the web.

Exploiting Format String Vulnerabilities Tutorial Pwn106 PWN101
Exploiting Format String Vulnerabilities ExamplesHet officiële Helpcentrum van Google Translate waar u tips en handleidingen voor het gebruik van het product en andere antwoorden op veelgestelde vragen kunt vinden. Met de Google Translate app kun je handgeschreven tekst foto s en spraak vertalen in meer dan 200 talen Je kunt Translate ook op het web gebruiken
Gallery for Exploiting Format String Vulnerabilities Examples
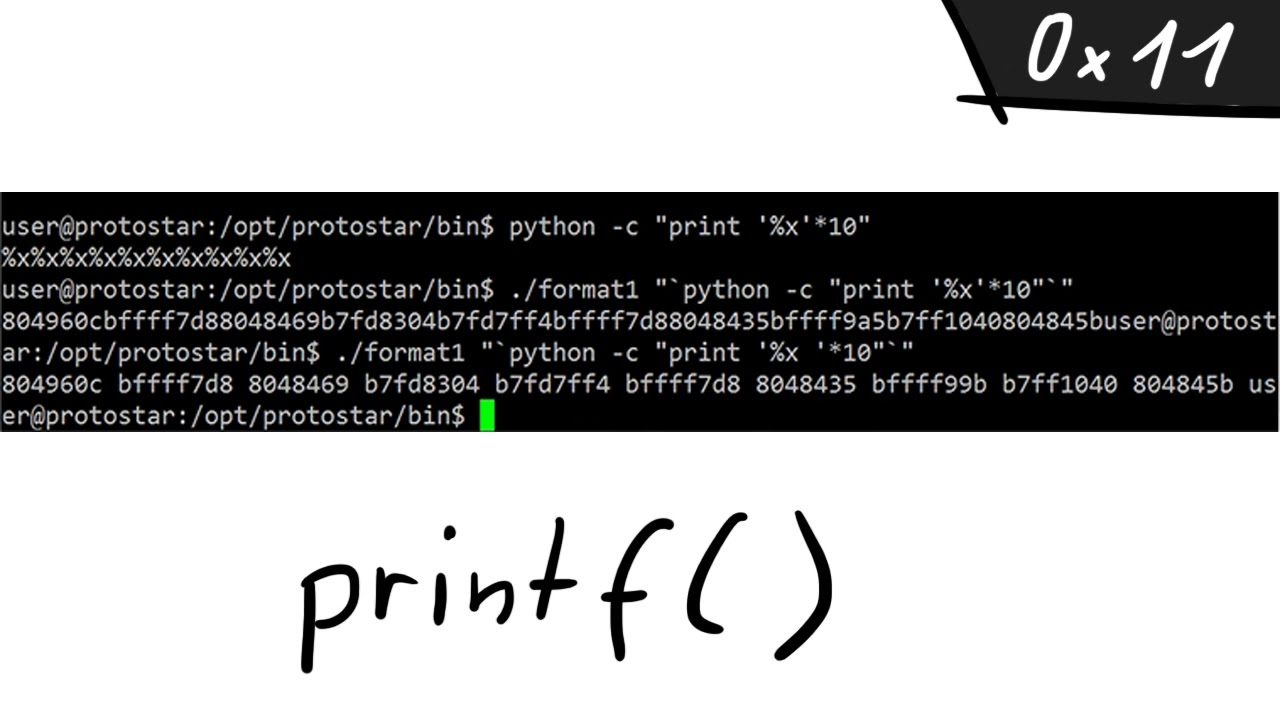
A Simple Format String Exploit Example Bin 0x11 YouTube

Explanation About Format String Vulnerabilities YouTube

Md Fahim Al Shihab Medium
Format String PPT
Format String PPT

Format String PPT

7 Uncensored Overflow Secrets Revealed DevMon Solutions

Basic Control Hijacking Attacks Ppt Download

Introduction To Information Security Spring 2016 Lecture 1

C Programming Printf Right Align