Elliptic Curve Cryptography Algorithm With Example
Planning ahead is the secret to staying organized and making the most of your time. A printable calendar is a straightforward but powerful tool to help you lay out important dates, deadlines, and personal goals for the entire year.
Stay Organized with Elliptic Curve Cryptography Algorithm With Example
The Printable Calendar 2025 offers a clear overview of the year, making it easy to mark appointments, vacations, and special events. You can pin it on your wall or keep it at your desk for quick reference anytime.
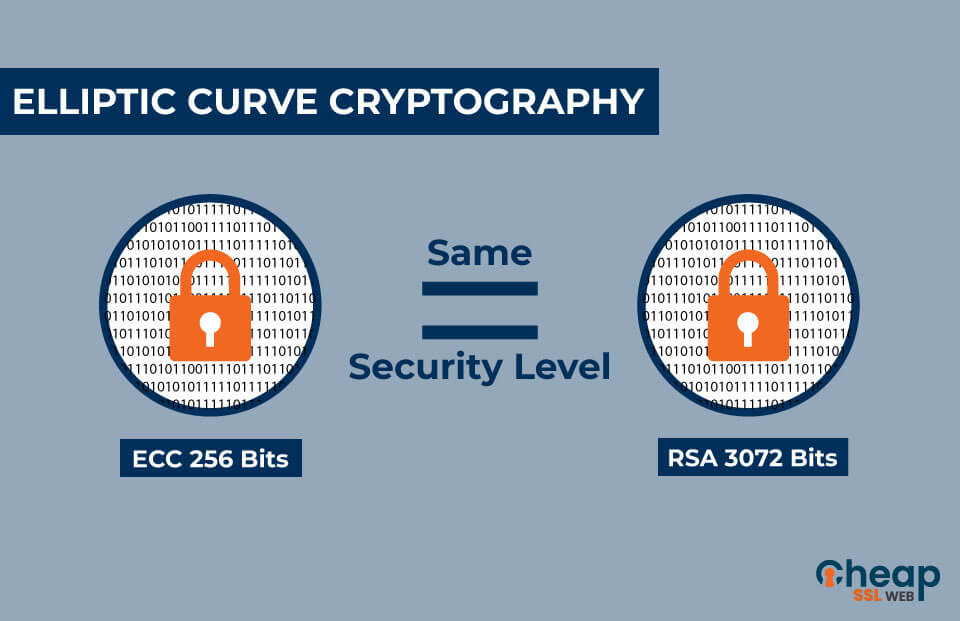
Elliptic Curve Cryptography Algorithm With Example
Choose from a variety of modern designs, from minimalist layouts to colorful, fun themes. These calendars are made to be easy to use and functional, so you can focus on planning without clutter.
Get a head start on your year by grabbing your favorite Printable Calendar 2025. Print it, personalize it, and take control of your schedule with clarity and ease.
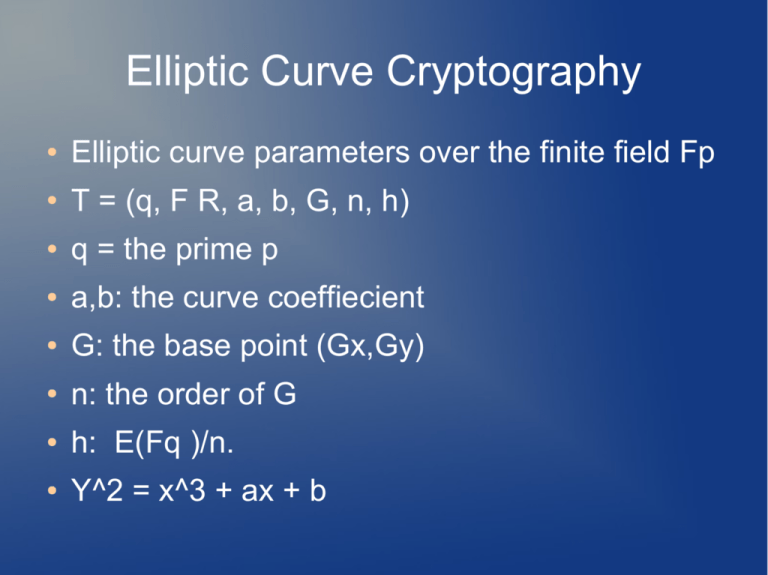
Elliptic Curve Cryptography
Abstract In this paper the mathematics behind the most famous crypto graphic systems is introduced These systems are compared in terms of secu rity e ciency and di culty of implementation Emphasis is given to elliptic curve cryptography methods which make use of more advanced mathematical concepts Contents Introduction Example of ECC public key (corresponding to the above private key, encoded in the Ethereum format, as hex with prefix 02 or 03) is: 0x02f54ba86dc1ccb5bed0224d23f01ed87e4a443c47fc690d7797a13d41d2340e1a.
Blockchain 101 Elliptic Curve Cryptography Paxos
Elliptic Curve Cryptography Algorithm With ExampleWe estimate the number of physical qubits and execution time by decomposing an implementation of Shor's algorithm for elliptic curve discrete logarithms into universal gate units at the logical ... Elliptic Curve Cryptography ECC is one of the most powerful but least understood types of cryptography in wide use today At CloudFlare we make extensive use of ECC to secure everything from our customers HTTPS connections to how we pass data between our data centers
Gallery for Elliptic Curve Cryptography Algorithm With Example

Elliptic Curve Cryptography ECC In Cryptography And Network Security

Symmetric Key Cryptography Secret Double Octopus

Elliptic Curve Cryptography Encryption And Decryption ECC In
The Proposed OSS Digital Signature Flowchart Based On Elliptic Curve
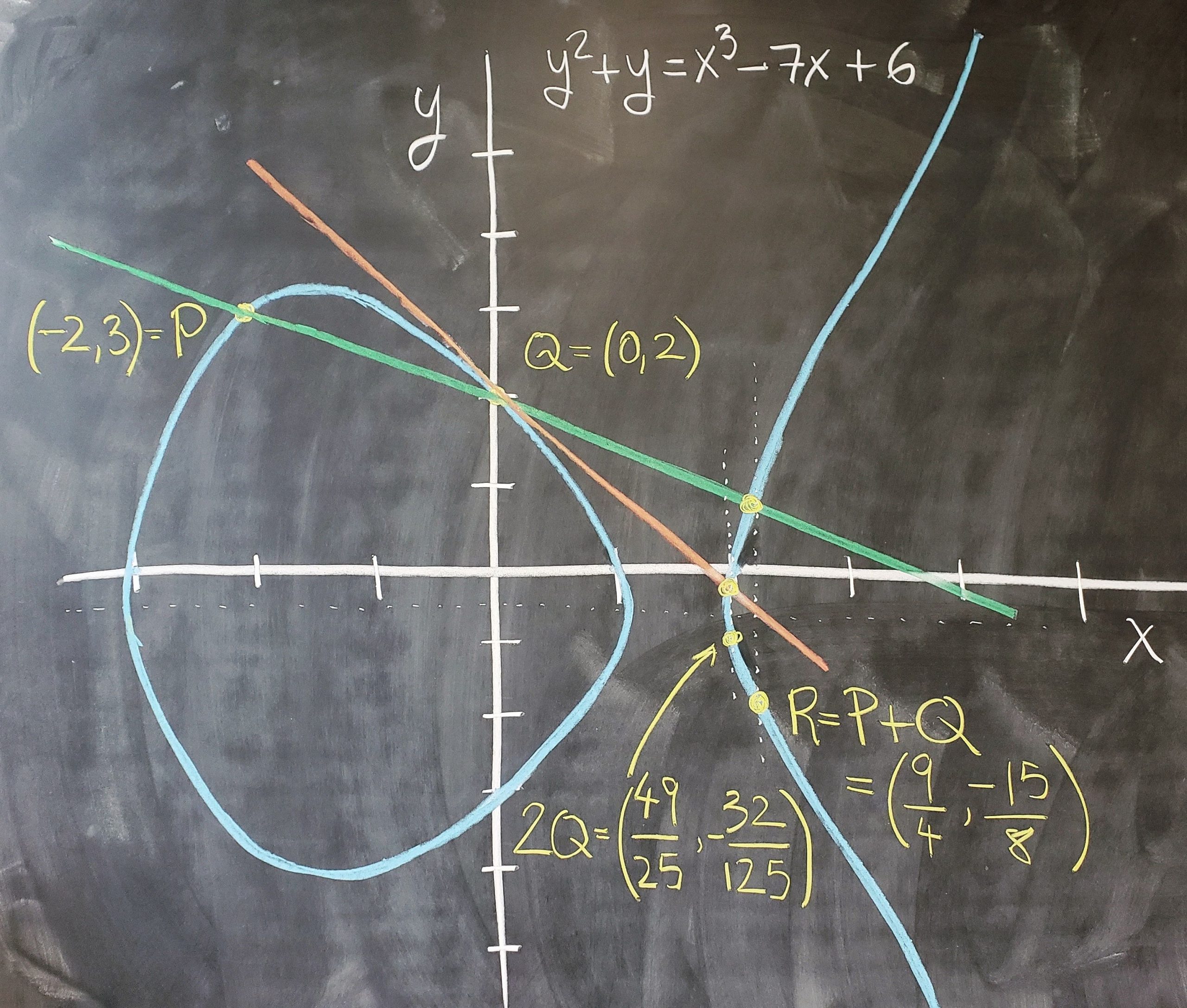
MATH 5020 The Arithmetic Of Elliptic Curves lvaro Lozano Robledo
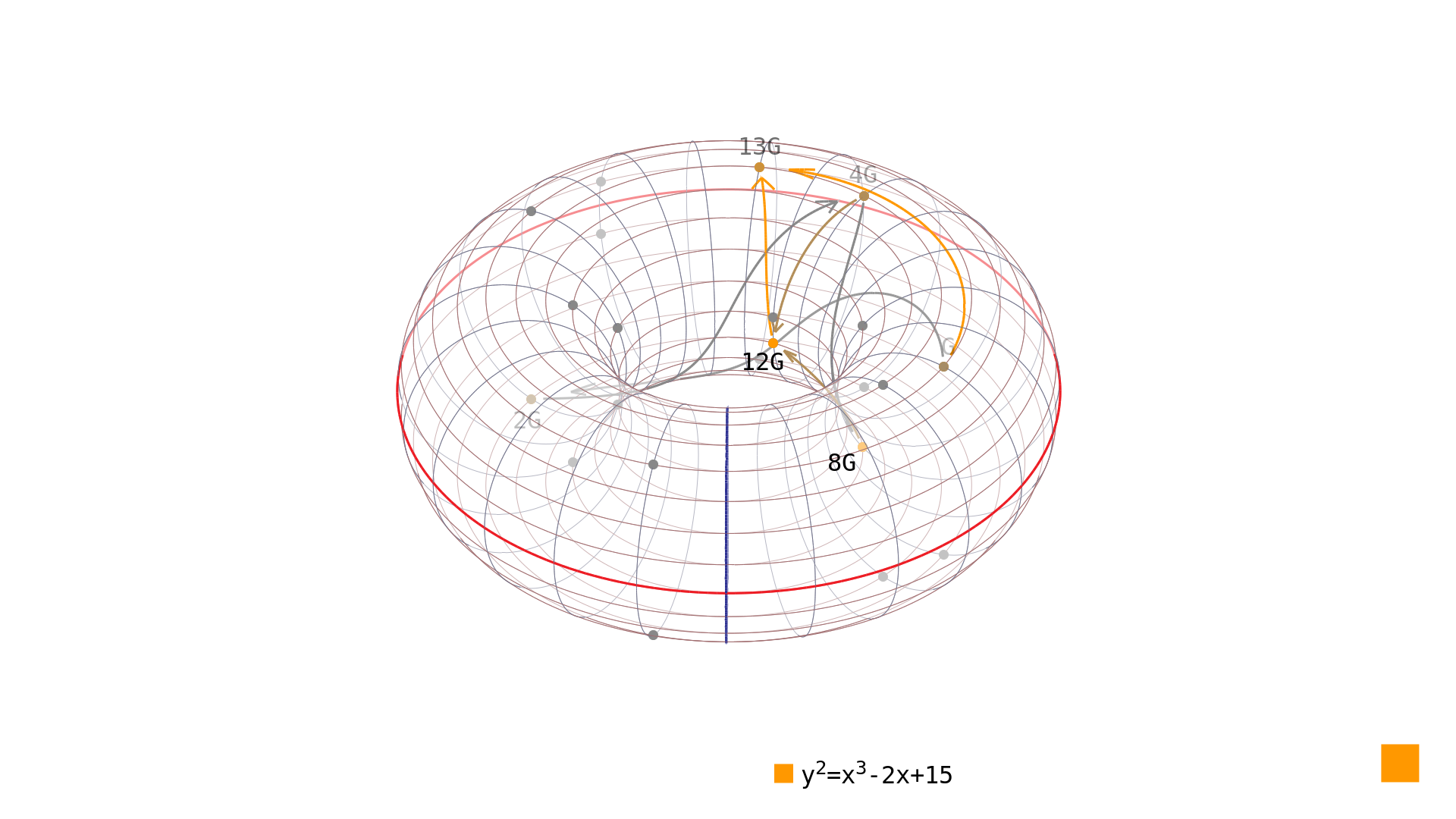
Trustica Elliptic Curves Discrete Logarithm Problem
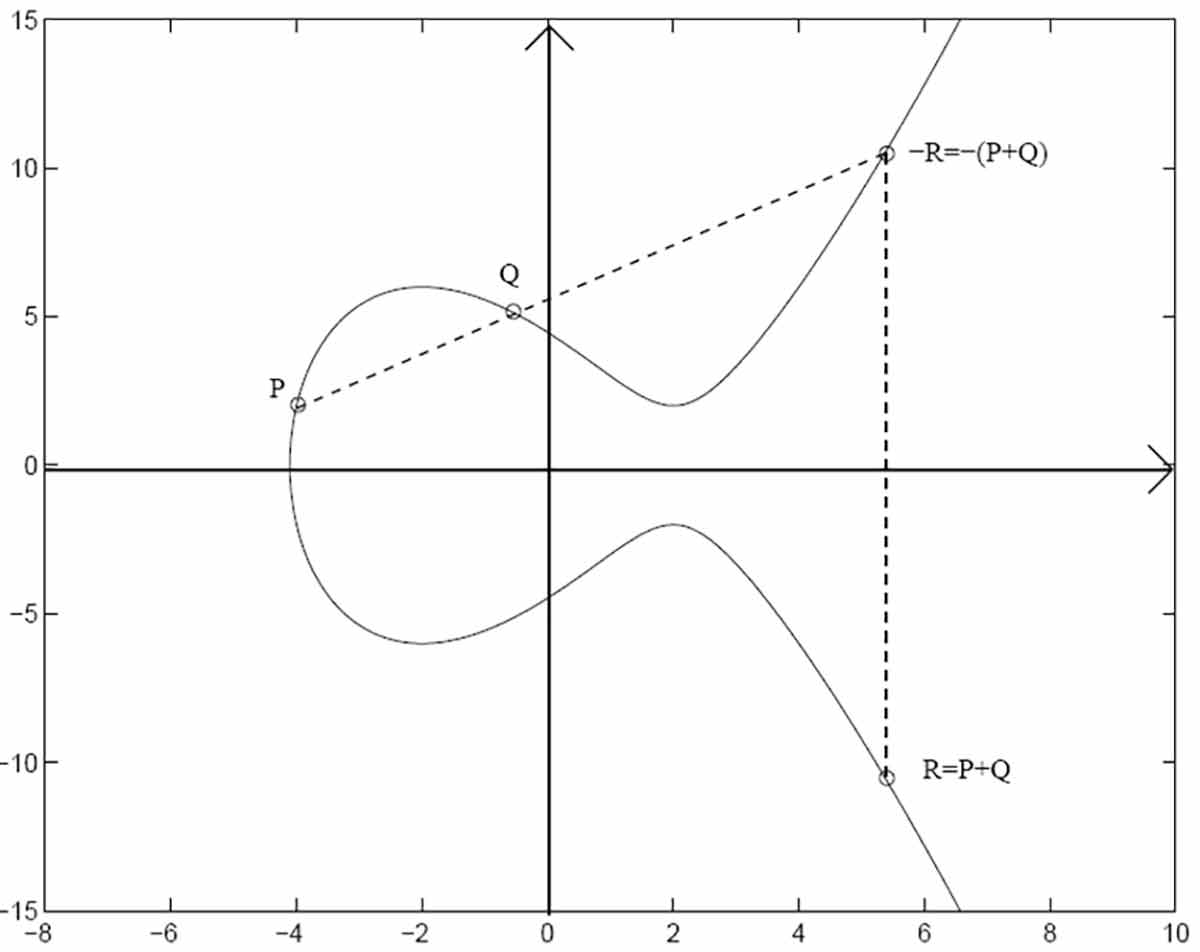
Elliptic Curve Cryptography Microsec en pki blog elliptic

Elliptic Curve Cryptography CyberHoot

Blog Posts Besttorrentrabco

Elliptic Curve Cryptography For Beginners